Preface
Just a year ago, when the LayerZero interoperability protocol's mainnet went live for just half a month, top-tier investment firms rushed to invest in it. On March 31, 2022, LayerZero announced the completion of a $135 million Series A+ funding round, led by a16z, FTX Ventures, and Sequoia Capital, with a valuation of $1 billion. In just one year, LayerZero once again raised $120 million at a valuation of $3 billion, triple the previous valuation. Investors include a16z, ChristiesInc, and Sequoia Capital, among others. Why is LayerZero attracting such attention from the capital market? This research report will provide a comprehensive analysis from the perspectives of mainstream models in the cross-chain sector, LayerZero's technical principles, cross-chain lifecycle, and the protocol's pros and cons. It aims to ultimately decipher the advantages that LayerZero possesses in this deterministic cross-chain landscape.
1️⃣Review of Mainstream Cross-Chain Models
✅What is a Cross-Chain Bridge? The formal definition of a cross-chain bridge is a tool that facilitates the transfer of assets (such as tokens) from a source chain to a destination chain. In practical applications, cross-chain bridges also exist for NFTs and information, and they enable the transfer of asset value rather than the assets themselves.
✅Why is Cross-Chain Needed? Over the past few years, there has been a significant increase in the number of sidechains, rollups, and layer-one blockchains that support and scale applications handling billions of dollars in value.
There are now over 126 various public chains. It can be said that the future of the decentralized world is multi-chain. However, there are currently limitations in terms of how information can be communicated and how interoperability can be achieved between different chains. It is a stage that has been tested but lacks a perfect solution.
During the rise of DeFi as the dominant trend, the evolution followed a path from assets to transactions, lending, and derivatives. To achieve these critical pathways, the demand for cross-chain solutions between different chains surged. During this period, a series of cross-chain solutions with their own advantages and disadvantages emerged for asset transfers. Cross-chain can be categorized into Asset Cross-Chain (ACB) and Arbitrary Message Cross-Chain (AMB). In this research report, we will first provide an overview of the mainstream asset cross-chain models in the past and then delve into the pros and cons of LayerZero as an arbitrary message cross-chain solution. Asset cross-chain issuance mechanisms mainly fall into two categories:
Price-anchored issuance: Anchoring the price of underlying assets.
Physical-anchored issuance: Anchoring the physical presence of the underlying assets.
1、Price-anchored Issuance
Essentially, when assets are issued on different chains, the liquidity is locked. It is similar to a central bank withdrawing old currency and issuing new currency of equal value. Since liquidity and value remain unchanged, price-anchored issuance is a classification based on the anchoring object. For example, $USDT is issued on various chains, and its price will always be anchored to the off-chain US Dollar. The assets are locked off-chain before and after cross-chain transfers (they are directly destroyed on-chain without a vault management module).
Mainstream models for maintaining price stability across different chains include:
1.1
Adjusting supply and demand ratios through algorithms (e.g., Basis Cash and Amplforth, Frax, Fei, and Float; although, in my opinion, trust in algorithmic stablecoins may be limited in the years following the UST's removal from its peg incident).
1.2
Combining over-collateralization with liquidation mechanisms to control price exchange risks.
Examples include DAI, a synthetic asset of MakerDAO, which is issued based on over-collateralization with multiple assets.
Another example is sBTC, a synthetic asset of Synthetix, which achieves price anchoring to Bitcoin through a highly collateralized ratio of over 750% of SNX (Synthetix ERC20).
For stablecoins, there is ultimately inherent risk associated with rigid redemption. In the past year, we witnessed the complete decoupling of UST from its peg and $USDC's near decoupling. This has led us to pay greater attention to asset cross-chain solutions based on physical anchoring.
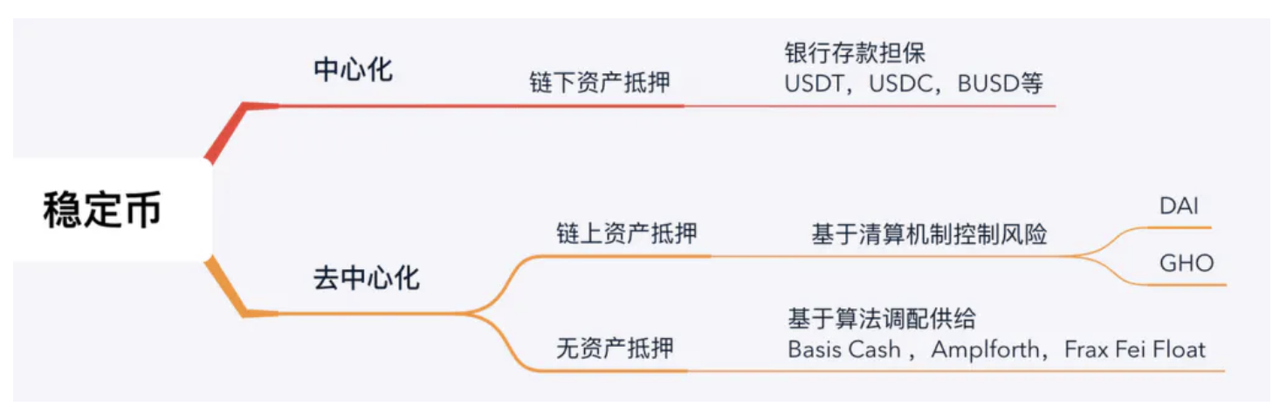
2、Physical-anchored Issuance
Physical-anchored issuance is the mainstream model for cross-chain asset issuance.
The core is based on the contract's trusted operability. The mainstream models involve locked minting cross-chain bridge patterns, liquidity bridge patterns, atomic swaps, sidechains/relay chains, etc. Even in the academic field, there is no unified naming convention for these solutions. In today's rapidly evolving industry, the classification and definition are usually based on the core patterns used by the systems. The following diagram by IOSG Ventures provides a summary of bridge solution categorization.
2.1
Overview of Cross-Chain Models
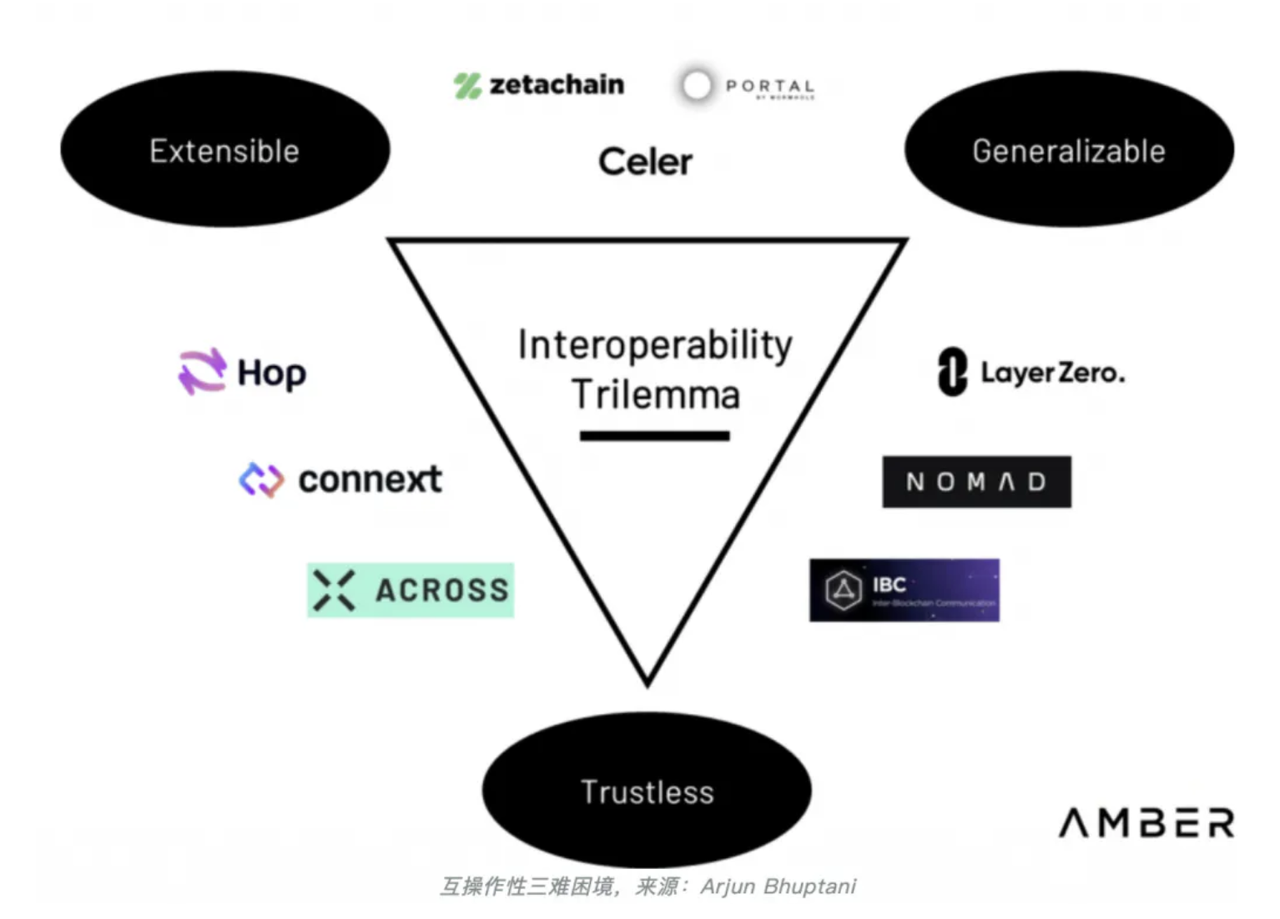
Similar to the impossibility triangle in public blockchains, achieving reliable interoperability in cross-chain solutions also involves compromises among the three dimensions of:
2.1.1
Universality:
The ability to transfer arbitrary data between two chains.
2.1.2
Scalability:
The ability to deploy quickly on heterogeneous chains.
2.1.3
Trustlessness:
Minimizing trust assumptions.
Therefore, we can see that LayerZero performs exceptionally well in terms of universality and scalability but compromises on trustlessness (depending on lightweight nodes and oracles). This will be further explained later in the discussion.
There are also triadic evaluation indicators proposed from different perspectives, which represent the difficulty of finding a perfect cross-chain solution:
Efficiently achieving finality (fast/reliable bridging from source chain to destination chain).
Cross-chain liquidity sharing (the degree of liquidity unification, such as whether multiple chains can share a pool on BSC).
Using native assets rather than wrapped/synthetic tokens (the type of assets obtained through cross-chain transfers). We will bypass complex solutions involving sidechains and relay chains and directly provide an overview of core models and their pros and cons. It's important to note that this article is focused on researching LayerZero, so there are many excellent cross-chain solutions that haven't been fully included in the comparison, such as Multichain, Synapse, Wormhole, Nomad, Celer Inter-chain Message (IM), Hyperlane, etc.
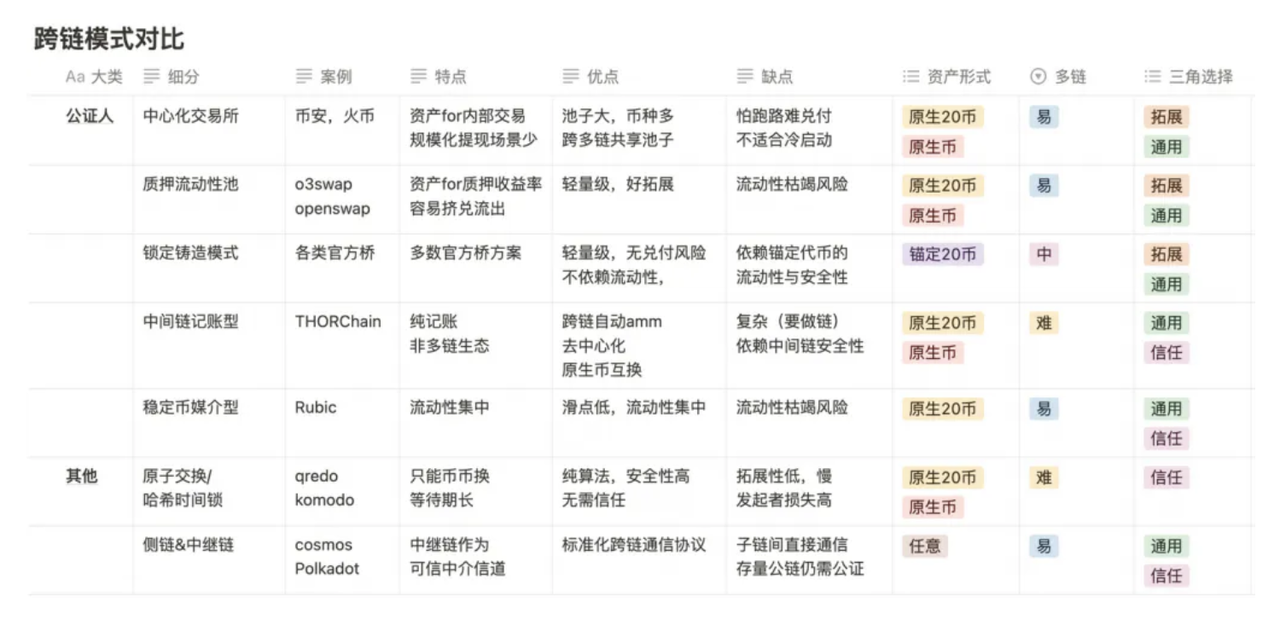
Additional explanation of the terminology used in the figure above: "Native coin" refers to base tokens used as fees, such as ETH and BTC. "Native 20 coin" refers to commonly used tokens that comply with the ERC20 standard and have a consensus, such as DAI, $USDC, etc. "Anchored 20 coin," also known as wrapped tokens, specifically refers to proof of eligibility for locked assets released equivalently during the cross-chain process, such as cETH, wDAI, etc.
2.2
Management Models of Validators
Whenever there is communication between different chains, it often relies heavily on validators. Validators represent a trusted source, whether it is in the context of cross-chain bridge models or liquidity bridge models (which can be further categorized into centralized exchange types, intermediary chain accounting types, stablecoin intermediary types, etc.).
The classification of validator management models is based on the number of signatures and the level of decentralization. It includes single-signature validators, multi-signature validators, and distributed signature validators.
Clearly, the management of private keys by validators is at the core of the trustworthiness of the entire scheme. The mainstream custody logic is as follows:
Centralized Custody: Single-signature validators and multi-signature validators. In cross-chain operations, only one or a few fixed participants' signatures are required for authorization. The underlying assets are held in a centralized manner, which poses lower security for funds. Multi-sig validators are generally composed of a consortium of institutions, and the transfer of cross-chain funds is completely controlled by this consortium.
Many past incidents of security breaches in cross-chain bridges were due to the theft of private keys held in centralized custody. For further reading:
https://mp.weixin.qq.com/s/c9OvVAaLUP6DH1MJQ0RbfQ
Distributed Custody: Distributed signature validators. Cross-chain operations require a fixed-size subset of nodes to collectively sign and authorize transactions. The underlying assets are held in a decentralized manner, providing higher security for funds. In essence, it adopts the concept of Secure Multi-Party Computation (sMPC), where validator nodes share custody keys through sMPC and threshold signatures. When a certain number or proportion of nodes provide partial signatures, they can reconstruct the complete signature. Thus, a minority of nodes working together maliciously cannot misappropriate the custody assets. Compared to the multi-signature validator mechanism, this approach offers higher security.
A typical example of a distributed signature validator mechanism is RenVM.
RenVM is a versatile, trustless, and permissionless decentralized custody network. It incorporates an economic incentive model and a dynamic fee mechanism to deter malicious nodes. It supports secure transfer of any asset from any blockchain to another blockchain platform. RenVM performs daily shuffling for random sharding. Each shard consists of at least 100 nodes, with shard nodes sharing custody keys through sMPC. When more than one-third of the nodes provide their signatures, the complete signature can be recovered. However, if fewer than one-third of the nodes collude, they cannot misappropriate the custody of digital assets.
3、Principle of Lock-and-Mint Cross-chain
As mentioned earlier, validators serve as the "Validator" component depicted in the diagram, responsible for verifying the authenticity of cross-chain asset transfers.
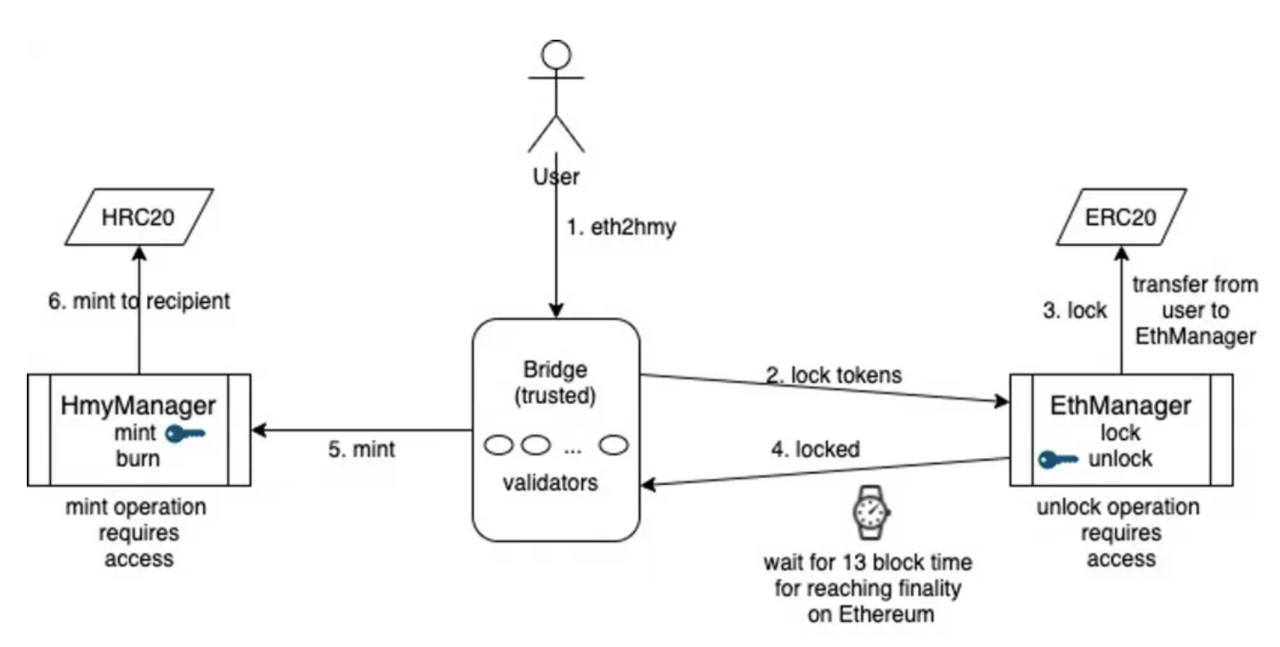
3.1 Trust Source of Lock-and-Mint Mechanism
Due to the immutability of contracts on blockchains, once a contract is deployed without any backdoors or reserved upgrade designs, there is no way to influence its operation. For example, if a contract transfers all permissions to address 0 and relinquishes ownership, there will be no way to mint new tokens, effectively locking the total liquidity of the contract. Similarly, even though contracts may differ across different public chains, if, on Ethereum, 10 ETH is locked using a contract, and on another trustworthy public chain, an equivalent contract releases 10 wETH, the overall liquidity is effectively fixed. As long as wETH can be transferred back to Ethereum at any time and exchanged for ETH, wETH can be considered to have equivalent value to ETH. Therefore, the core operations are:
Lock-and-Mint: Chain A locks token liquidity + Chain B issues an equivalent wrapped token for circulation.
Burn-and-Release: Chain B burns the wrapped token + Chain A unlocks an equivalent amount of base tokens' liquidity.
Validators are responsible for detecting the locking event on Chain A and minting anchored tokens on Chain B, which are then transferred to the target address.
In summary, although the operations and logic are simple, the fundamental trust lies in the redemption capability. In the event of a cross-chain bridge breach or asset imbalance, some participants may be unable to withdraw their assets. This anticipation of inevitability leads to a run on the bridge and ultimately its collapse.
3.2
The Core Challenges of Lock-and-Mint Mechanism
Apart from the trustworthiness of validators, the most critical issue with the lock-and-mint cross-chain bridge is that the received tokens are not native tokens.
In the lock-and-mint mechanism of a cross-chain bridge, when a user completes a cross-chain transaction, they receive wrapped tokens representing the anchored value, such as WETH instead of ETH. However, the issuance of these wrapped tokens can only be authorized by multiple validators. Consequently, the usability of tokens obtained after cross-chain transactions remains limited.
Advantages are clear: through the step-by-step operations mentioned above, it is evident that the lock-and-mint approach is highly suitable for one-sided or single-asset bridging. Hence, it has become the mainstream solution for various official cross-chain bridges in new blockchain projects, as it leverages the official identity to justify the use of wrapped tokens, making it both simple and intuitive.
However, there are significant disadvantages as well. The mechanism of wrapped tokens often necessitates an additional interaction with a dexPool, such as UniSwap, for the tokens to flow smoothly. This introduces the impact of trading pool exchanges on transaction slippage and additional gas consumption from the extra transaction. For further reading: Understanding Impermanent Loss in DEX: Principles, Mechanisms, and Formula Derivation.
In conclusion, the core challenges of this approach lie in the trust cost for users and the risks associated with safeguarding high TVL (Total Value Locked).
4、Principle of Liquidity Bridging
After understanding the lock-and-mint approach mentioned earlier, the concept of liquidity bridging becomes easier to comprehend since its main point revolves around obtaining native tokens. In this case, the term "minting" is replaced with "releasing." Users receive LP tokens that represent the native tokens provided on their respective chains, and the LPs earn dividends from the transaction fees of the cross-chain bridge.
On the other hand, the significant disadvantage lies in the user-friendly aspect, which is also subject to risks resulting from LP dynamics. The liquidity depletion becomes the determining factor for the survival of the entire bridge, especially when it comes to comparing asset staking yields. Moreover, the earnings obtained by LPs highly depend on the balance of funds from both sides. If a majority of assets tend to cross to one side, LPs become more concerned about the risk of exchange, leading to a potential run on the bridge.
From the perspective of funding sources and dividend distribution after liquidity is locked, further categorization can be made:
4.1 Centralized Exchange Model:
Funding originates from internal trading demand without the need for dividend distribution, but the risk of centralization is higher.
4.2 Staked Liquidity Pool Model:
Funding originates from LP injections and requires dividend distribution. The liquidity of cross-chain assets depends on the size of the liquidity pool.
4.3 Stablecoin Mediator Model:
Funding originates from LP injections. Before cross-chain transactions, stablecoins are exchanged through a DEX to reduce slippage.
5、Principle of Atomic Swaps/Hash Time-Locked Cross-Chain
The principle of atomic swaps/hash time-locked contracts (HTLC) is often associated with the use of time locks. It relies on creating a Hashed Timelock Contract to facilitate the atomic exchange of digital assets between different blockchains in a decentralized manner. The basic process of atomic swaps for cross-chain transactions is as follows:
Two participants, Alice and Bob, agree on the assets and quantities for the cross-chain transaction.
Alice randomly generates a key S and calculates H=hash(S). She then creates an HTLC contract on her blockchain (Chain A) and locks her assets in the contract (including the hash value H and a timeout period).
Alice sends the hash value to Bob, who creates an HTLC contract on his blockchain (Chain B) using the same hash value and locks his assets in the contract.
Bob decrypts the hash value and sends the decrypted result to Alice as the transaction password.
Alice uses this password to unlock the assets in the HTLC contract created by Bob and unlocks her own assets.
Bob uses the same password to unlock the assets in the HTLC contract created by Alice and unlocks his own assets. The transaction is completed.
The transaction is completed.
It is evident that if Alice wants to receive the LTC sent by Bob, she needs to disclose S. In this case, Bob can use the same S to receive the BTC sent by Alice. If S is not disclosed, neither Alice nor Bob can receive the digital assets sent by the other party. They can only retrieve their original assets, meaning both transactions are either successful or unsuccessful. If either party fails to complete the transaction within the timeout period, the contract will be canceled, and the assets will be returned to their original accounts, ensuring the security and reliability of the transaction.
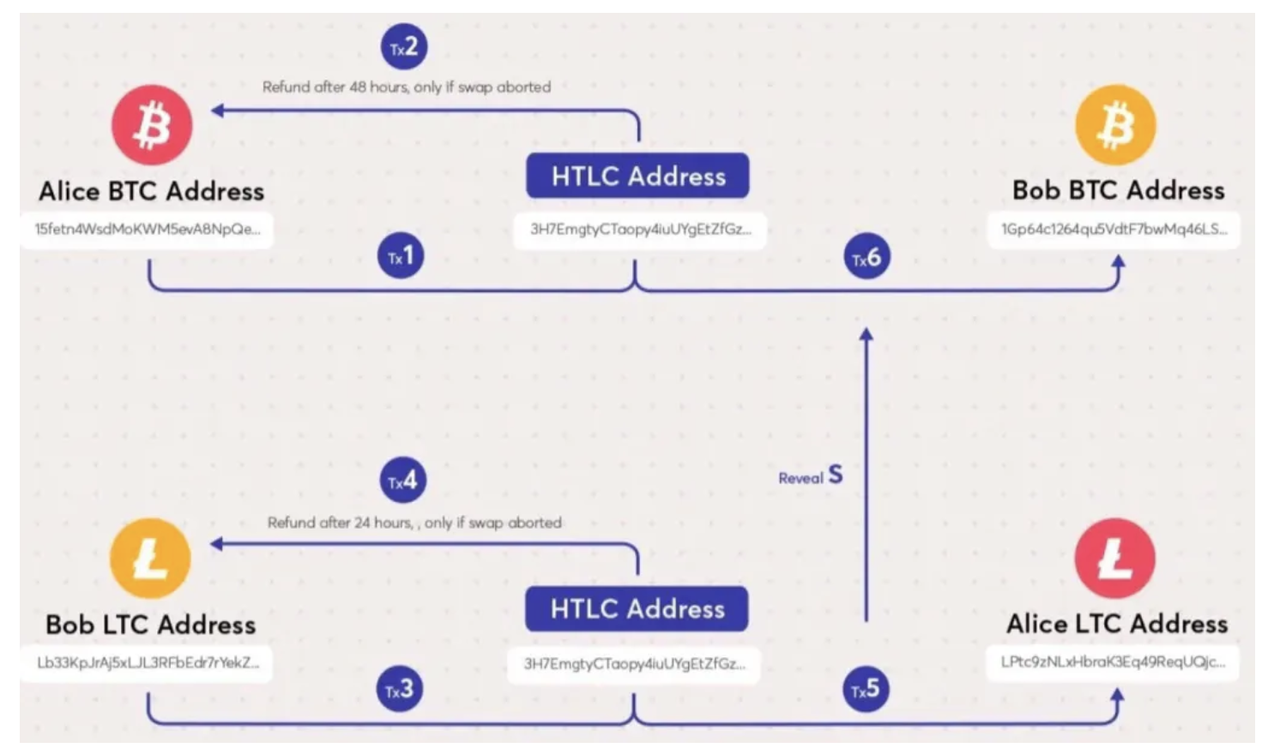
Although atomic swaps for cross-chain transactions are secure and reliable, they have some drawbacks:
Restrictive: Atomic swaps for cross-chain transactions can only be performed between blockchains that support the same hash function, limiting their applicability.
Time-consuming: Atomic swaps for cross-chain transactions require a certain amount of time to complete since they need to wait for the timeout period, which may affect transaction speed. They also suffer from the inconvenience of free choice, as participants can withdraw at any time.
Transaction limitations: Atomic swaps for cross-chain transactions only support "like-kind exchange" of assets, meaning the value of the assets must be equal. This may limit the flexibility and availability of transactions.
Difficulty in scalability: The solution for atomic swaps in cross-chain transactions is challenging to scale to large-scale transactions. It is more suitable for token-to-token exchanges rather than asset anchoring issuance or information cross-chain transactions, as token-to-token exchanges rely on price information.
Despite the drawbacks, atomic swaps for cross-chain transactions remain a highly secure and reliable method, especially when trustless transactions are required. After all, there is no need for centralized roles like intermediaries throughout the process, which eliminates trust-related risks.
✅Summary
Finally, let's compare the three cross-chain models in the following diagram, each with its own advantages and disadvantages.
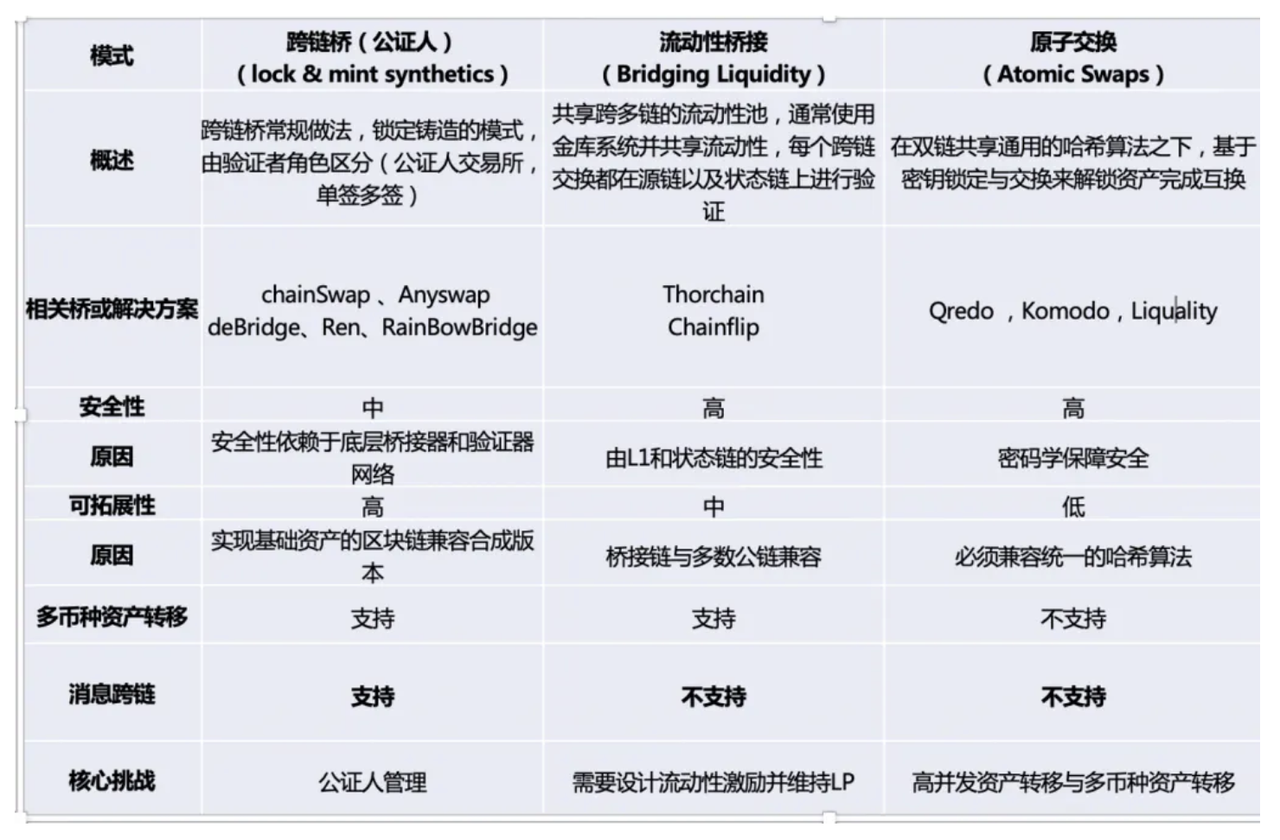
In this research report, we have omitted the equally fascinating sidechain and relay chain models. This is because Cosmos and Polkadot have both implemented cross-chain communication protocols in their underlying blockchain platforms, seamlessly supporting communication between subchains within their respective ecosystems. However, integrating existing blockchain platforms still requires the use of various bridging solutions mentioned earlier.
2️⃣ Why is LayerZero worth attention?
To achieve interoperability of assets across multiple chains, the aforementioned solutions have been competing for years, each with its own advantages and disadvantages, without a clear winner. Let's return to the core research objective of this article, LayerZero, and review its three funding events:
On September 16, 2021, LayerZero completed a $6 million Series A funding round, led by Multicoin and Binance Labs, with participation from Sino Global Capital, Defiance, Delphi Digital, Robot Ventures, Spartan, Hypersphere Ventures, Protocol Ventures, Gen Block Capital, Echelon Capital.
On March 31, 2022, LayerZero Labs announced the completion of a $135 million Series A+ funding round, led by FTX Ventures, Sequoia Capital, and a16z, with participation from Coinbase Ventures, PayPal Ventures, Tiger Global, and Uniswap Labs, among others. The post-money valuation reached $1 billion.
On April 4, 2023, LayerZero Labs raised $120 million in a Series B funding round at a valuation of $3 billion. Participants included a16z Crypto, Christie's, Sequoia Capital, Samsung Next, BOND, Circle Ventures, and OpenSea Ventures.
With top-tier investment banks, substantial funding, high growth rates, and rapid fundraising speed, LayerZero has once again captured the author's attention. Let's delve into its underlying principles and analyze its advantages in this deterministic cross-chain competition.
3️⃣ Deep Dive into LayerZero's Technical Principles
If I were to provide an overview of LayerZero:
LayerZero is a trustless cross-chain communication protocol. Its essence lies in utilizing the principles of light nodes and designing a mechanism for ultra-light nodes, splitting the trust portion into two parts through relays and oracles, thereby achieving better security at a lower cost.
It is important to note that LayerZero's focus is not asset cross-chain, but rather message cross-chain at a higher layer. As a foundational protocol, it encompasses the application layer of asset cross-chain. More specifically, asset cross-chain is also developed by LayerZero Labs through Stargate.
💥 What is a Light Node?
The communication between cross-chains is mainly achieved through external verification or on-chain light nodes.
The notaries mentioned earlier are simple forms of external verification mechanisms. Similarly, Cosmos and Polkadot also employ external verification mechanisms, albeit with a heavier focus on using chains to enhance communication security.
So, what role do on-chain light nodes play?
First, a light node is a mode of node operation, similar to full nodes and archive nodes.
In blockchain, the current block is connected to the previous block, forming a chain of trust. Different nodes on the same chain store a reduced version of the chain's information. Light nodes only keep the block headers from history and do not store the specific transaction information within the blocks.
With multiple Merkle Roots derived from block headers, the authenticity of a transaction in a block can be verified using Merkle tree validation.
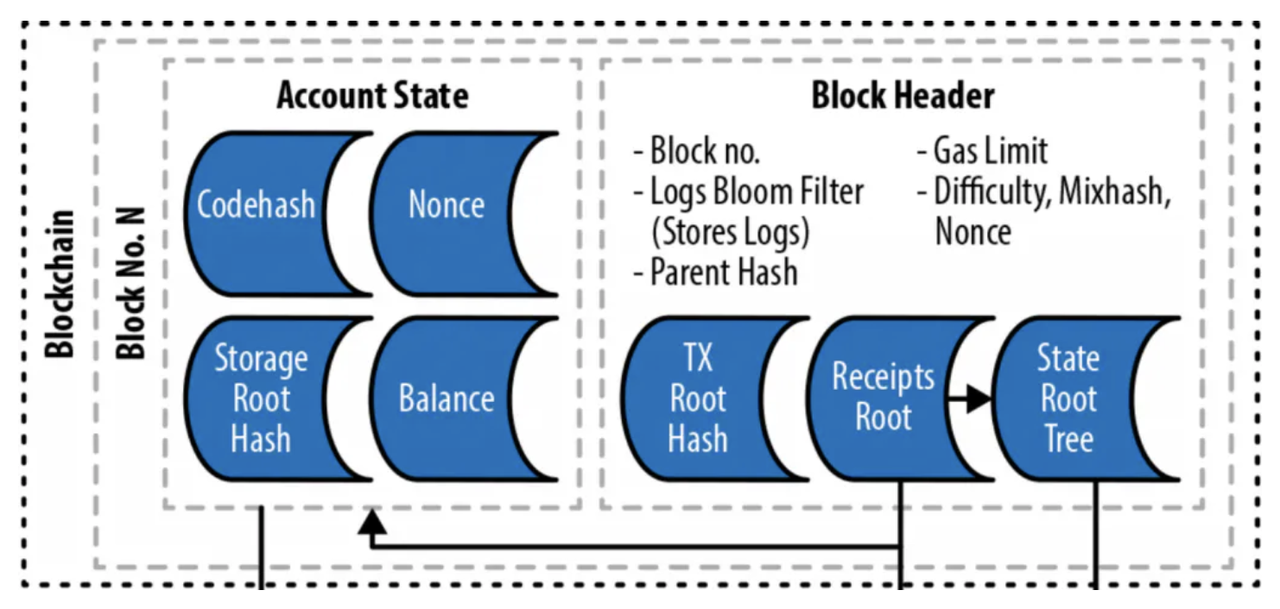
Therefore, compared to the data scale of 1 TB for a full node and 10 TB for an archive node, a light node with only 10 GB is considered quite lightweight. However, even with just 10 GB, fully validating and verifying all the data on the chain is still a challenging and costly task.
The benefit of running validation on-chain using light nodes is the complete elimination of external roles like notaries, achieving a high degree of decentralization based on the chain's inherent security, thus enhancing overall security.
However, this reliance on cross-chain incurs additional costs, which will ultimately be borne by the users with cross-chain needs. The author once estimated the cost of NFT metadata storage per kilobyte and further exploration can be found in the articlehttps://mp.weixin.qq.com/s/610rn9B2-hg8Bd88W-viXA
The conclusion is that adding 1 KB of data storage on the chain would cost 640,000 gas, which translates to $25 when converted to currency: 20 * (640,000) * 1e9 / 1e18 * 2000 = $25.
💥 What is an Ultra-Light Node?
An Ultra-Light Node (ULN), as the name suggests, is a simple concept. In comparison to a light node, an ultra-light node performs the same validations as an on-chain light node but does not retain all block headers in sequential order. Instead, it receives them in a streaming manner from distributed oracles as needed.
The benefit of an ultra-light node is that it does not rely on a sequential data flow of block headers starting from the genesis block. Additionally, the cost of storing this data on-chain is shared between oracles and relayers.
The trade-off with an ultra-light node is the lack of a historical sequential data stream. This means that if both oracles and relayers engage in malicious behavior simultaneously, malicious information could be executed due to the lack of verification.
The trade-off between a certain degree of security loss and a significant reduction in costs depends on each party's individual considerations based on their specific scenarios. The design of social protocols, such as the Lens Protocol, can provide valuable insights on how to optimistically execute meta-transactions and perform post-execution tracing while maintaining proper application layer isolation for social-focused information, where the value of information is not significant.
💥 The Cross-Chain Core Roles of LayerZero
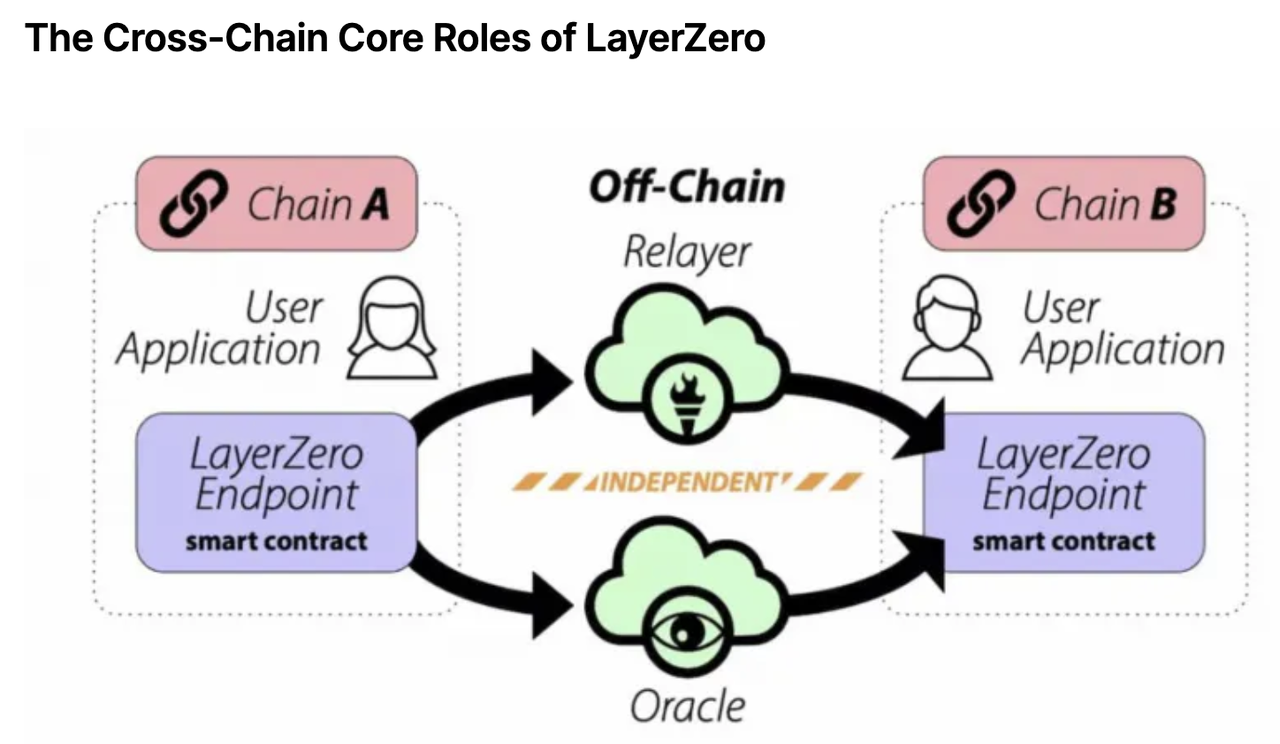
In the official LayerZero whitepaper diagram above, the green-colored sections represent the key roles that facilitate information exchange between two chains. In the official LayerZero whitepaper diagram, the green portions represent the key roles that facilitate information exchange between two chains: Oracle and Relayer.
💥 Positioning of Oracle and Relayer
Simply put, the primary role of an Oracle is to inform the contracts on the target chain when to verify and what the verification result is. On the other hand, a Relayer is responsible for providing the proof process required for verifying transactions and the specific content of cross-chain information. The term "Oracle" can be puzzling, as it does not imply predicting the future. Rather, it refers to an off-chain infrastructure that brings data into the blockchain. It has diverse applications, including smart contracts, insurance, financial markets, and more. For example:
Smart Contracts: An Oracle can provide real-world weather data.
Insurance: In the insurance industry, an Oracle can be used to trigger insurance claims, among other events.
Financial Markets: In the realm of financial markets, an Oracle can provide real-time data, such as stock prices and exchange rates.
In my previous research article on ERC-4337, I also mentioned that the current ERC-4337 contract requires integration with off-chain Oracle price services to achieve multi-currency payment transaction fee functionality. For further reading, please refer to the articlehttps://research.web3caff.com/zh/archives/6900?ref=shisi In summary, an Oracle serves as the notary role in LayerZero's cross-chain interactions. Considering the malicious motivations that may arise, the security of an Oracle is nearly equivalent to the value of DeFi on the blockchain. As many lending products rely on Oracles to provide prices, if an Oracle were willing to act maliciously, there are other high-profit activities they could engage in.
💥 Division of Labor between Oracle and Relayer
The role of an Oracle is to transmit the Blockhash and Block Receiptsroot of a cross-chain request on the source chain to the target chain.
Blockhash: A block hash that informs the contracts on the target chain which block contains the user's cross-chain request.
Block Receiptsroot: Used to verify the messages transmitted by the transaction relayer. The role of a Relayer is to transmit the Receipt and Merkle Proof of the cross-chain message, along with the required path information, to the contracts on the target chain for verification.
The Receipt refers to the transaction receipt information, which primarily includes the transaction execution result, transaction hash, and transaction event logs.
Transaction execution result: Indicates whether the transaction on the source chain was successful.
Transaction hash: The globally unique hash for each transaction.
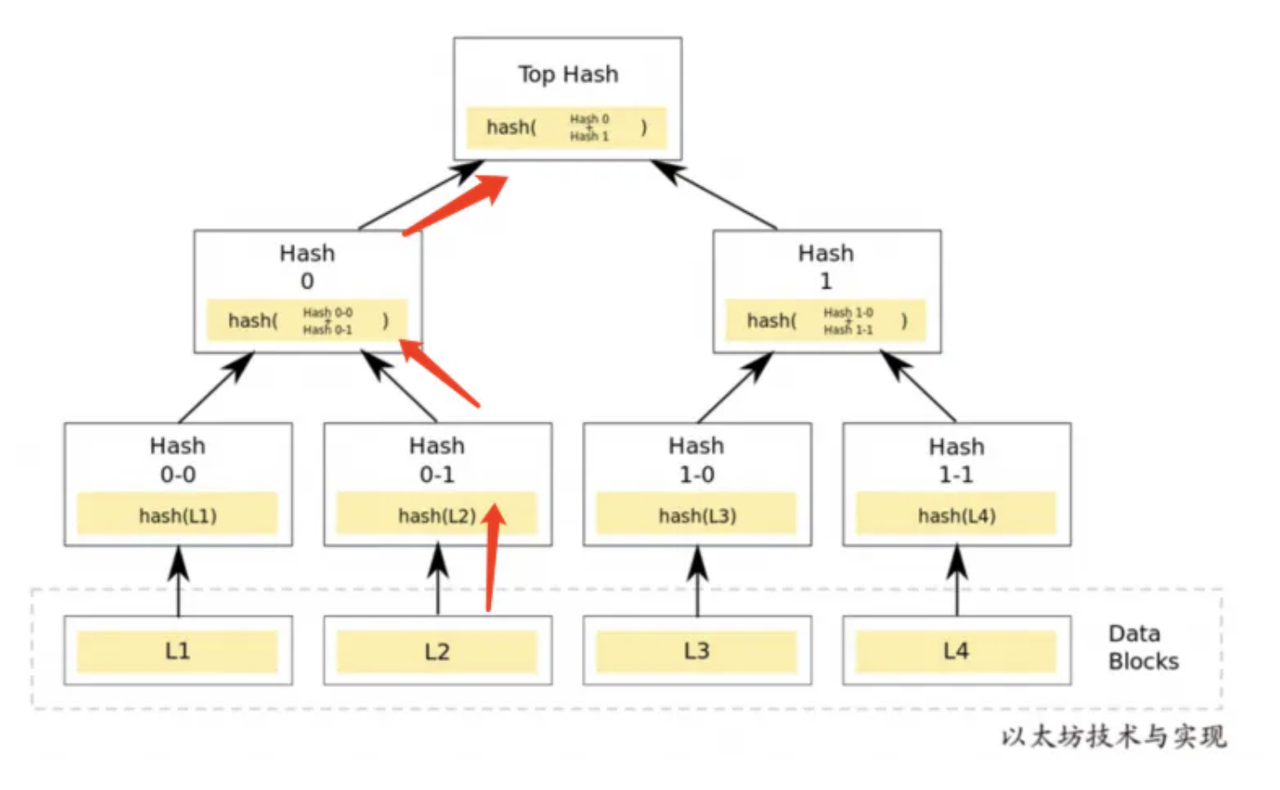
Transaction event logs: Specific details regarding the cross-chain information. The path information referred to here is represented by the red arrows in the diagram below. For example, the relayer sequentially conveys the information of L2 -> Hash 0-0 -> Hash 1 to the nodes on the chain. By comparing the TopHash provided by the Oracle and performing secondary calculations based on the information provided by the relayer, if the results are consistent, then the relayer can be considered correct.
💥 The Cross-chain Lifecycle on LayerZero
Now that we understand the roles of cross-chain components in the intermediate region, let's examine a transaction from Chain A to Chain B. In the diagram below, the two boxes on the left and right represent interactions with endpoint contracts on their respective chains.
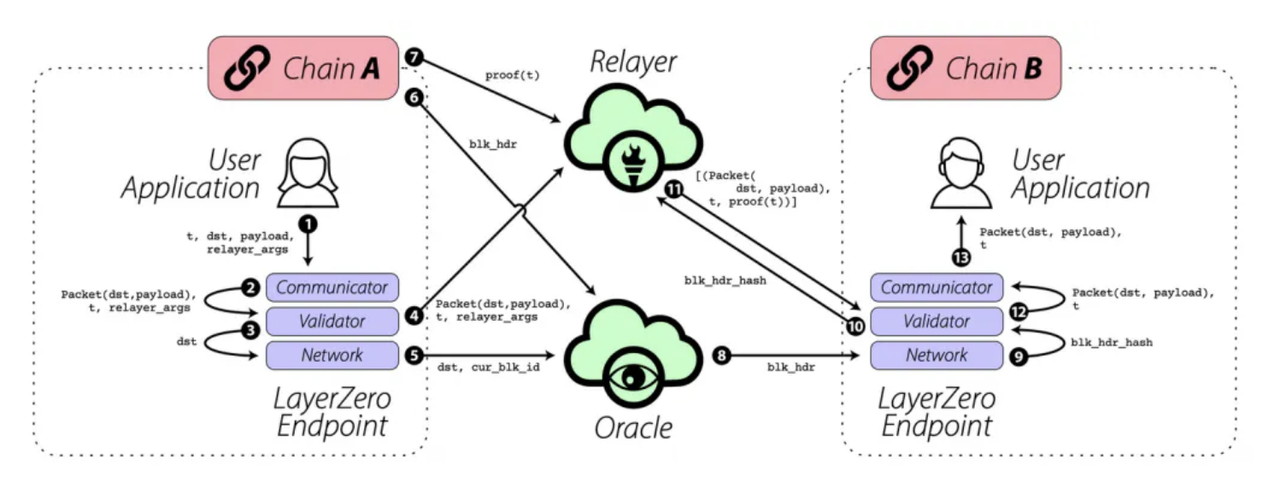
Here is an overview of the overall process:
A transaction is initiated by a user application (UA), which triggers an action on the blockchain. With the assistance of Oracles and Relayers within LayerZero endpoints, the transaction is broken down into multiple parts (proofs and block headers). Once the Oracles and Relayers send their respective information to the target chain (signing the transaction), and the LayerZero Endpoint contracts validate the information, the message is converted and executed on the target chain.
The detailed steps are as follows (refer to the diagram for reference):
Step 1: The user application UA (e.g., Stargate Bridge) communicates with the LayerZero Communicator, sending a request that includes the transaction identifier t, the data for the transfer from A to B (payload), and identifiers for the user application smart contract or relayer on Chain B (relayer_args), among other transaction details.
Step 2: The Communicator sends this data as a LayerZero packet to the Validator.
Step 3: The Validator sends the transaction identifier and the identifier of the smart contract on Chain B to the Networking layer. The Networking layer is triggered and waits for the information to be passed from the source chain A to the target chain B via an Oracle.
Step 4: The Validator forwards this information (packet) to the Relayer. Once notified, the Relayer retrieves the transaction proof (Step 7) from off-chain storage and sends it to Chain B (Step 11). The endpoint on Chain B can also initiate a request to obtain the result for a specified block hash (Step 10).
Step 5: The Networking layer sends the identifier of the smart contract on Chain B and the block ID of the transaction block to the Oracle. When notified, the Oracle retrieves the block header of the current block on Chain A (Step 6) and sends it to Chain B (Step 8).
Notably, Steps 6, 7, 8, 10, and 11 are all executed within the processes of the Relayer and Oracle.
Step 9: The Networking layer sends the retrieved block hash to the Validator, triggering validation by the light node.
Step 12: The Validator ensures that the transaction is valid and submitted by examining the transaction proof and block header stored in the Networking layer. If the block header and transaction proof match, the transaction information (Packet) is sent back to the Communicator.
Step 13: The Communicator forwards the information (Packet) to the user application on Chain B, enabling it to perform any desired function.
Gas fees for the overall cross-chain process are levied on the source chain when the initial transaction is executed, while on the target chain, fees are associated with the three components: Relayer, Oracle, and Layer Zero: Executor (an EOA account).
💥 Overview of the Application Layer on LayerZero
Radiant Capital is a LayerZero-based full-chain lending protocol that enables users to deposit collateral on Chain A and borrow assets on Chain B. Essentially, it facilitates cross-chain asset transfers.
Cashmere Labs, which is yet to be launched, consists of two primary products: stablecoin trading and a cross-chain DEX aggregator with resistance against MEV (Miner Extractable Value). The main technological attribute protecting against MEV is that arbitrageurs cannot access order information during interchain messaging, thus preventing frontrunning and sandwich attacks related to MEV.
OmniBTC is a LayerZero-based cross-chain DEX aggregator. For instance, it utilizes the Stargate cross-chain bridge to exchange $USDT on Ethereum for $USDT on the BNB Chain, and then executes the trade on PancakeSwap for BNB.
Stargate, a core application layer product of LayerZero,
Currently, it supports interoperability between eight major public blockchains. The operational mode involves opening vault accounts on each chain. When users deposit assets on the source chain, Stargate utilizes the LayerZero communication protocol to facilitate cross-chain requests to the target chain, ultimately ensuring cash-out to the designated user account on the target chain.
Based on the categorization method of validators and asset types mentioned earlier, Stargate can be defined as a validator that utilizes LayerZero as a specific case (relay + oracle). The asset type consists of the original 20 tokens, involving asset management dividends related to LPs. Additionally, it is designed to facilitate stablecoin-mediated cross-chain transactions for the purpose of unifying liquidity pools.
One innovative aspect is the consideration of $USDT and $USDC as 1:1 assets. This means that if a user deposits 1000 $USDC on Ethereum, they can withdraw approximately 994 $USDT on Arbitrum (with a 6 $USDT fee).
This presents a challenge for Stargate since the use of native assets and unified liquidity makes ensuring immediate settlement somewhat difficult. When multiple transactions occur concurrently and deplete the liquidity pool, users are unable to perform cross-chain withdrawals. The conventional approach is to provide a token like "anyUSDC" as future withdrawal proof until more $USDC is deposited to enable native asset redemption, as done by platforms such as Multichain.
Stargate resolves this issue through a combination of algorithmic balance and manual intervention. It dynamically adjusts the liquidity depth in different LP pools and regulates the supply mode to mitigate the depletion of pools.
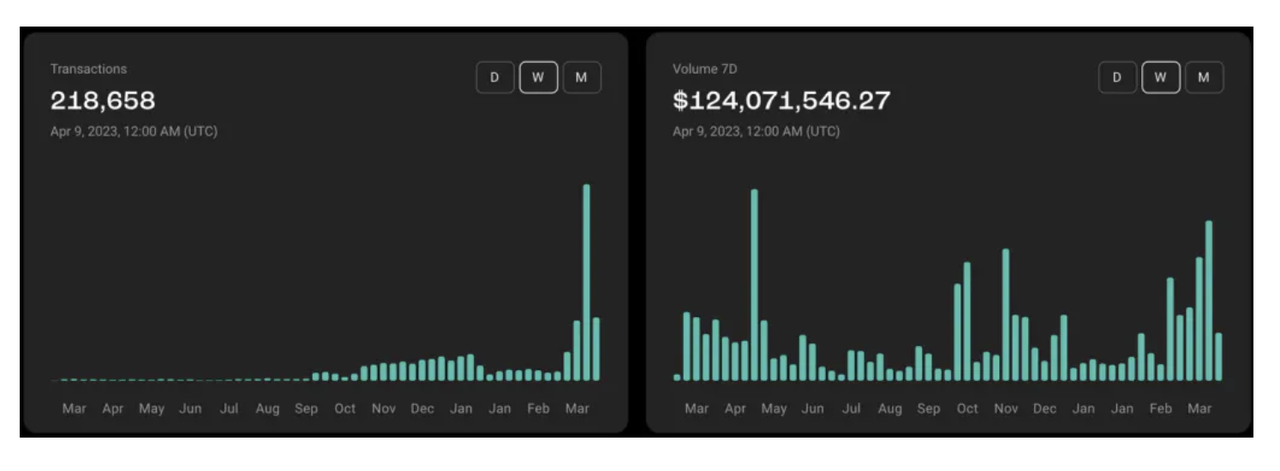
The current total value locked (TVL) depth of Stargate has decreased significantly compared to its peak last year, currently stabilizing at around $400 million. The overall trading volume tends to fluctuate in response to various hot events on multiple target chains.
4️⃣ How to evaluate LayerZero?
4.1 Positioning of the LayerZero Protocol
I must say that the name is well chosen. "Layer 0" has been a term in the industry, primarily used to refer to the protocol at the network transport layer. If we consider blockchain networks as Layer 1 (such as Bitcoin, Ethereum, BSC, etc.), then the protocol responsible for network communication within the blockchain network should reside below Layer 1, hence referred to as Layer 0.
A similar analogy can be drawn to traditional internet protocols. Teams like bloXroute, NYM, Marlin, and others have optimized the underlying transmission methods of the internet for privacy and network efficiency, which is what most people understand as Layer 0.
The Oracle and Relayer components in the LayerZero protocol also transmit messages between blockchains, but it diverges slightly from the previously perceived concept of Layer 0 as an internet's underlying transmission protocol. LayerZero's focus lies more in the "communication" of information between blockchains.
Currently, the market's application of cross-chain technology mainly revolves around asset cross-chain transfer.
However, asset cross-chain transfer is just a small subset of the entire cross-chain technology. In fact, many cross-chain bridge products used before were hastily developed transitional solutions to meet the basic needs of users in response to the emergence of multi-chain ecosystems.
To enter a truly mature multi-chain ecosystem where users can seamlessly interact with all major public chains through a single application—without the need for frequent wallet switching—convenience and smoothness are necessary components of the future vision. Therefore, a protocol-level cross-chain product that enables information cross-chain transfer, rather than simple asset cross-chain transfer, is essential.
In summary, the positioning and essence of the protocol are not limited to a single asset cross-chain bridge but revolve around achieving full-chain information connectivity, which is crucial for accommodating billions of users in the future.
4.2 Pros and Cons of the LayerZero
4.2.1
Security: Is it dangerous to rely on prophecy?
If there is only one Relayer or one Seer, it may be dangerous (it is not the domain of the protocol itself), but LayerZero currently implements that any application can customize its own Relayer or choose different seers to support its system.
Even if some Relayer breaks down or does not work or works incorrectly for some purpose, in the gradual market competition, a many-to-many choice pattern will be formed, and decentralized mutual supervision will be formed between their respective games just like the miner mechanism.
Even if Prophet 1 and repeater A maliciously collude, this is an isolated risk because only applications that use both Prophet 1 as A predictor and repeater A as a message will be affected.
And LayerZero is only the lowest layer of information transmission mechanism, as for information transmission, the use of upper-layer applications can be defined and reinforced separately. As for the protocol itself, it does not store money, nor does it store data, which makes it less likely to be attacked itself.
Therefore, because the money is dispersed, the cost of hacking becomes higher and the return is smaller.
LayerZero has been officially reviewed for more than 58 versions, including Quantstamp, Zokyo, Zellic, and Trail of Bits. In addition, he currently hosts a $15 million bug bounty through ImmuneFi, the largest real-time bug bounty program in the entire industry! To date, LayerZero has awarded nearly $1 million to white hats that have made disclosures.
4.2.2
Compare the advantages of protocol layer cross-chain products
Consistent with the previous conclusion, the very low cross-chain security verification cost is a highlight, the same loss is the security of the highly trusted prophet, in addition to the security factor (after all, can be hardened at the application layer), versatility and very low protocol access costs for developers are a major hidden advantage.
4.2.3
Greater general extensibility
In today's protocol layer cross-chain, there are Cosmos ecosystem IBC protocol and Boka ecosystem XCMP cross-chain protocol, the reason why they are limited in scalability is that for Ethereum to verify the transactions of other public chains, the corresponding light node must be deployed on Ethereum. This high Gas cost makes it difficult for many EVM compatible chains (ETH/BSC/Polygon/L2, etc.) to support the IBC protocol, which greatly limits the commonality of the IBC protocol, so it can still only run between relatively niche Cosmos ecological chains.
4.2.4
Lower developer access complexity
From the beginning, the workload of the underlying protocol was placed on the minimalist contract access design, and the demand scenarios for messages across the chain were extremely high, such as cross-chain lending, revenue aggregation, and trading were just the beginning. Because it is easy to develop, the protocol has so far delivered more than 2 million messages across more than 30 on-chain DApps, including decentralized exchanges PancakeSwap, SushiSwap, TraderJoe, and Uniswap. And the application bridge on it has locked in a total value of more than $7 billion.
4.2.5
Remove the compatibility of multi-chain fragmentation
In the previously mentioned lock casting model, the generated packaged tokens are a fragmentation phenomenon of multi-chain funds, while LayerZero uses a non-encapsulated asset approach, can support EVM and non-EVM, and a unified liquidity layer. As well as the ability to bundle complex transactions such as original chain exchange, bridge, target chain exchange, and pledge when assets cross the chain.
5️⃣ Why is the capital chase LayerZero?
The first reason is cross-chain certainty, which is a rare high-certainty role in the multi-chain landscape, which can expand the business with the birth of a new chain, and bear little risk when the new chain fails, because the protocol itself does not carry assets. The second is a clear business model, and the current head cross-chain bridge has a good revenue. For example, the annual revenue of Multichain in 2021 is 17 million US dollars, which has exceeded the protocol revenue of Dex Dragon Curve in the same period. The revenue source is charging fees from cross-chain sales, and the average market Take Rate is 0.05%. For example, in Stargate, an asset cross-chain bridge implemented on LayerZero, users will have to pay 0.06% for each use. The specific allocation is:
0.01% is paid to liquidity providers as an incentive, which can be understood as interest paid by banks to depositors, but also as a cost.
0.01% is given to holders of the pledged token veSTG, which can be understood as a dividend paid by the bank to its shareholders.
0.04% belongs to the national Treasury and ecological construction expenses.
If you start from the traditional investment perspective, you can continue to calculate its PE (P/E ratio refers to the ratio of market value to the company's net profit), PS (market sales ratio refers to the ratio of market value to sales revenue), There was an agency in September 22 at a market value of 1 billion estimated the result is to reach 300 times PS (note that based on Stargate cross-chain bridge revenue).
In contrast, other models in this track have not perfectly broken through the impossible triangle, or high operating costs, or centralization leads to insecurity, or can not meet the needs of multiple assets.
Finally, the omnichain full-chain development trend, with the help of Layerzero, $USDC can be faster and cheaper on the chain of native cross-chain, which means that $USDC has become a full-chain asset. Full-chain assets refer to the cost, speed and risk of assets across the chain are greatly reduced, and assets will be able to flow freely across multiple chains.
In summary, cross-chain is one of the important tracks in the multi-chain pattern, the future is high certainty, the business model is clear, and the market is still immature stage has high revenue, as a communication protocol embedded in the basic code of various Dapps, the protocol itself has become one of the bottom of LEGO bricks.
